Month: February 2014
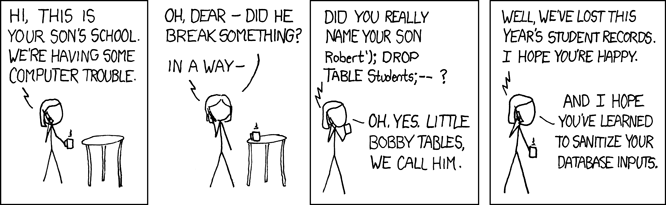
What is a SQL Injection attack?
Two days ago I interviewed a developer that was applying for a junior software developer position.
One of the questions that every interviewer must always ask is about the security of the data.
So, the developer answered the question by referring me to this comic: